5 Reasons Why Operational Technology (OT) Security Needs a Different Platform
Blog / 4 min read / Saurav Singh

A $43 billion company stops production for weeks. Not by a natural disaster. Not by supply chain collapse. By cyberattack. But how? This blog post discusses the multiple advantages of using an integrated cybersecurity solution, as well as its effectiveness in combating changing cyber threats.
In May 2025, Nucor Corporation - North America's largest steel producer - was forced to halt production at multiple facilities after detecting unauthorized access to its IT systems GBHackersSteel Industry News. Attackers successfully exfiltrated data from the company's systems Steel Industry News, disrupting operations across the U.S., Mexico, and Canada.
Steel mills that operate 24/7 - some with furnaces that can't simply be "turned off" without causing millions in equipment damage - sat idle while security teams scrambled to contain the breach
The pattern is clear: OT is not IT.
If you’re a CISO today, your job probably doesn’t stop protecting data and networks. Increasingly, it includes safeguarding the systems that run your business - the machinery that produces goods, moves materials, and powers operations.
That world is called Operational Technology (OT), and it’s very different from IT. Yet, many organizations still try to secure OT with the same tools and tactics used for corporate systems - and quickly discover that it doesn’t work.
Here’s why OT requires a different approach, and what that means for your business.
1. OT Was Never Meant to Be Connected
Most OT devices like industrial controllers and turbines - were designed decades ago to run safely in isolation. The assumption was simple: if it’s not connected, it can’t be hacked.
But with digital transformation driving connectivity between IT and OT, these once-isolated systems are now part of the corporate network. That connectivity brings value - better insights, efficiency, and uptime - but it also exposes systems that were never built with security in mind.
Business Impact: If compromised, these systems can stop production lines, disrupt operations, or even endanger safety. 60% of industrial organizations experienced at least one OT network intrusion in the past year (Fortinet 2024 State of OT & Cybersecurity Report).
2. The Equipment Is Old - and That’s Okay (According to Leadership)
In IT, devices get replaced every few years. In OT, that same controller might still be running perfectly after 20. The problem?
It’s running on outdated software that can’t be patched or upgraded without stopping production.
Replacing it isn’t as simple as swapping a laptop - it requires downtime, vendor certification, and testing to avoid disrupting operations.
Business Impact: Legacy systems are a hidden cost center. They make the environment harder to protect, increase insurance and compliance costs, and limit how fast the business can modernize safely. 58% of manufacturers say legacy equipment is their top OT security challenge (Fortinet, 2024).
3. Scanning Can Do More Harm Than Good
In IT, running a vulnerability scan is standard practice. In OT, that same scan could knock a device offline. Industrial systems aren’t designed to handle probing or aggressive traffic. Even a harmless discovery scan can crash into a controller or sensor, halting production and triggering safety systems.
Business Impact: Unplanned downtime in manufacturing can cost thousands of dollars per minute. A single misconfigured IT scan could lead to millions of production losses, delayed shipments, or missed SLAs.
4. The Priorities Are Different: AIC, Not CIA
In IT, we talk about Confidentiality, Integrity, Availability (CIA). In OT, the order is reversed: Availability, Integrity, Confidentiality (AIC).
- Availability is everything - if systems go down, production stops.
- Integrity ensures that machines perform as intended. Even a minor deviation - say, a robotic arm using the wrong sealant - could trigger product recalls or safety issues.
- Confidentiality matters, but mostly for protecting intellectual property and operational data.
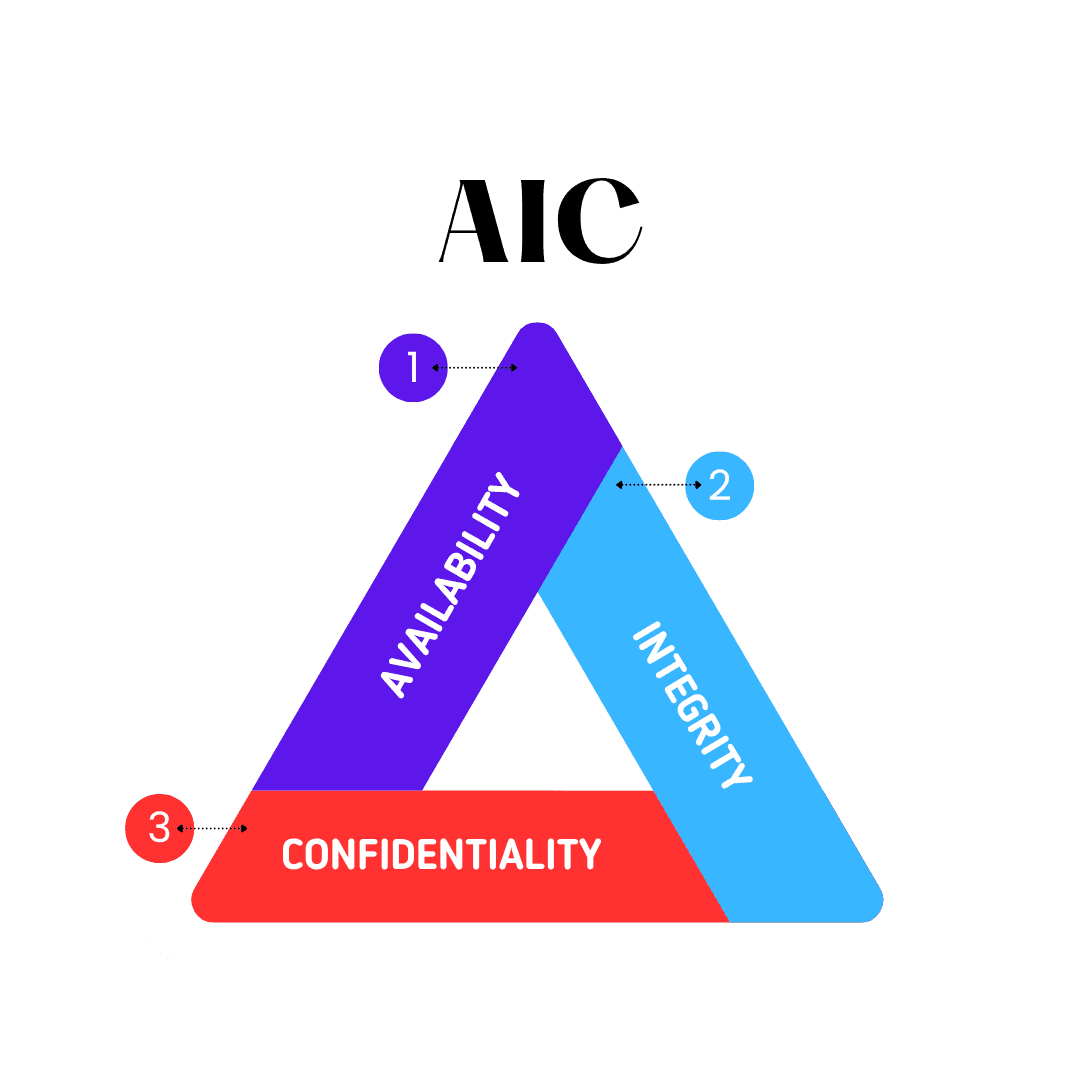
Business Impact: IT security focuses on protecting data; OT security protects revenue, safety, and brand reputation. Getting the balance wrong can mean prioritizing the wrong risks.
5. IT Tools Weren’t Built for OT Platform
Most IT security tools assume that systems can be restarted, patched, and actively monitored. OT environments don’t have that luxury - they run continuously, often 24/7, with devices that can’t tolerate interference.
Trying to apply IT security directly to OT can result in false positives, network disruptions, and operational slowdowns.
That’s why dedicated OT security platforms are purpose-built to deliver visibility, threat detection, and risk reduction - all without interrupting operations.
Business Impact: Purpose-built OT security tools reduce operational risk while maintaining uptime, improve compliance posture, and give CISOs the visibility needed to make informed investment and insurance decisions.
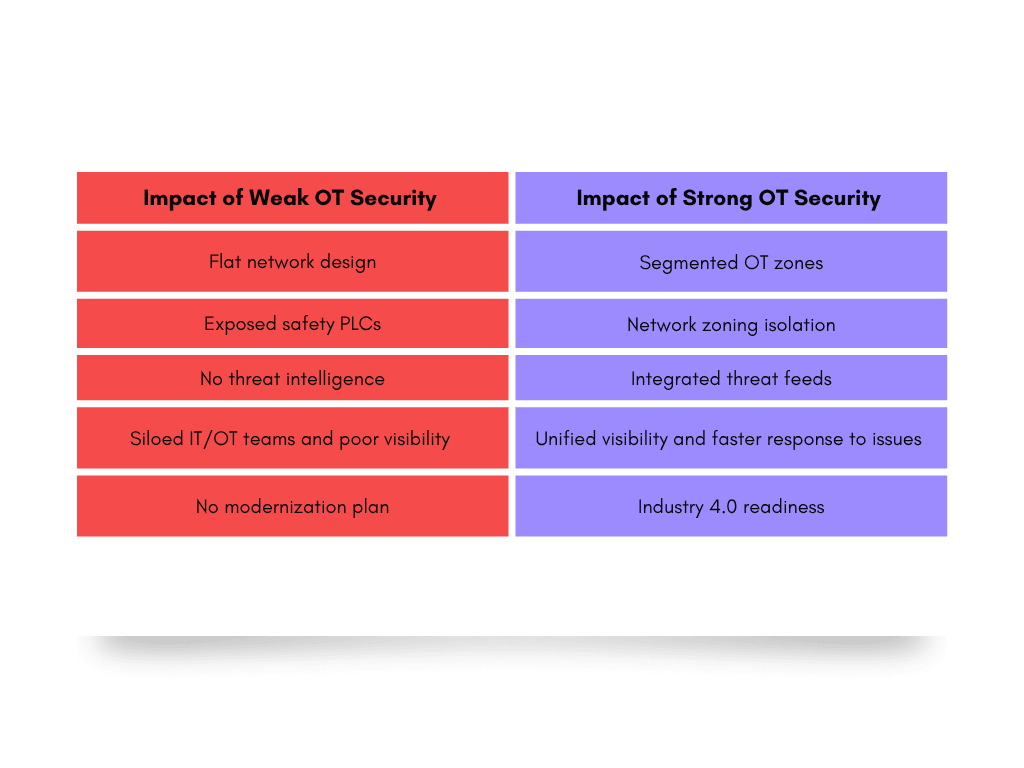
Business Impact of Getting OT Security Right
For CISOs, OT security isn’t just another technical project - it’s a business enabler. Here’s what’s at stake:
See How ZeroHack OT Protects OT Without Production Risk
Book a 30-minute demo to see how leading manufacturers achieve complete OT visibility while maintaining 24/7 uptime. Watch real threats detected in real-time - with zero operational disruption.



