Modern power grids form the backbone of global infrastructure, ensuring essential services from hospitals to transportation run smoothly. Yet today, the OT systems managing these critical networks have become prime targets for sophisticated cyber threats. This blog post discusses the multiple advantages of using an integrated cybersecurity solution, as well as its effectiveness in combating changing cyber threats.
According to recent trends, the current landscape paints an alarming picture:
- ShadowPad malware, linked to Chinese group TAG-38, targeted seven SLDCs in northern India via compromised devices. While no disruption occurred, the incident highlights the growing cyber threat to power infrastructure and the need for stronger ICS defenses.
- China-linked RedEcho targeted 10 Indian power sector assets, including SLDCs and key ports, using persistent malware infrastructure. While no disruption was reported, the attack highlights long-term espionage risks and the need for stronger ICS cybersecurity in the energy sector.
- A Maharashtra Cyber Cell probe confirmed that malware caused the October 2020 Mumbai blackout, with 14 Trojan Horses and 8GB of suspicious data found in MSEB systems. Though no country was officially blamed, U.S. reports pointed to possible Chinese involvement, highlighting the urgent need for stronger ICS cybersecurity.
(Source: https://www.indiatoday.in/india/story/maharashtra-cyber-cell-mumbai-power-outrage-1774522-2021-03-01)
Key Threats
- State-Sponsored Cyberattacks
- Advanced Persistent Threats (APTs) targeting national grid systems.
- Aim to create blackouts, cause chaos, or extract sensitive data.
- SCADA System Exploitation
- Hackers manipulate control systems to switch off power, trip breakers, or cause equipment failures.
- Target protocols like Modbus, DNP3, and IEC 104.
- Remote Access Vulnerabilities
- Weak VPNs, RDP, or exposed ports allow unauthorized access to OT environments.
- Often caused by misconfiguration or lack of access control.
- Legacy Devices
- PLCs, IEDs, and RTUs are decades old and lack modern security features.
- Cannot be patched or monitored easily.
- Insider Threats
- Malicious or careless insiders with privileged access can disable protections or alter controls.
- Includes contractors, vendors, or disgruntled employees.
Real-World Attack Example: Colonial Pipeline (2021)
- Type of Attack: Ransomware (DarkSide group)
- Entry Point: Corporate IT network, but OT systems were shut down proactively
- Impact:
- Shutdown of fuel distribution to the Eastern U.S.
- Panic buying and fuel shortages in multiple states
- $4.4 million ransom paid
- National emergency declared by the U.S. government
Impacts of Cyberattacks on the Power Sector
Grid Blackouts
Tampered commands can collapse entire regions, affecting hospitals, airports, and emergency services.
Fuel Supply Disruption
Attacks on control systems of refineries or pipelines can halt energy flow.
Equipment Damage
Incorrect voltage, current, or frequency commands can destroy transformers and generators.
Environmental Hazards
Failures in pressure, gas, or temperature controls can cause explosions or hazardous leaks.
Regulatory Penalties
Fines and legal action for non-compliance with NERC CIP, TSA, or ISO standards.
Public Confidence Loss
Prolonged outages or safety events damage trust in government and infrastructure operators.
General Defense Strategy (Best Practices)
-
Network Segmentation
1. Isolate OT systems from IT and the internet using firewalls and DMZs. 2. Use VLANs to segment internal OT zones. -
Access Controls & MFA
1. Implement strict role-based access. 2. Enforce multi-factor authentication for all remote connections. -
Patch & Vulnerability Management
1. Regularly update software and firmware on OT systems where possible. 2. Use virtual patching if updates are not available. -
Intrusion Detection & Monitoring
1. Deploy OT-specific IDS/IPS to detect SCADA anomalies. 2. Monitor critical control commands and unauthorized changes. -
Endpoint Hardening
1. Disable unused ports and services. 2. Restrict USB and peripheral use on engineering workstations. -
Secure Remote Access
1. Use encrypted VPNs with jump servers and session recording. 2. Allow access only during defined time windows. -
Incident Response Plans
1. Develop and test scenarios like grid outages, ransomware attacks, and SCADA compromise. -
Employee Training
1. Educate engineers and operators on phishing, USB safety, and cyber hygiene. -
Offline Backups
1. Maintain secure offline backups of critical configurations and control logic.
To overcome this presenting, you India’s first complete OT security portfolio – built for power, precision & resilience: 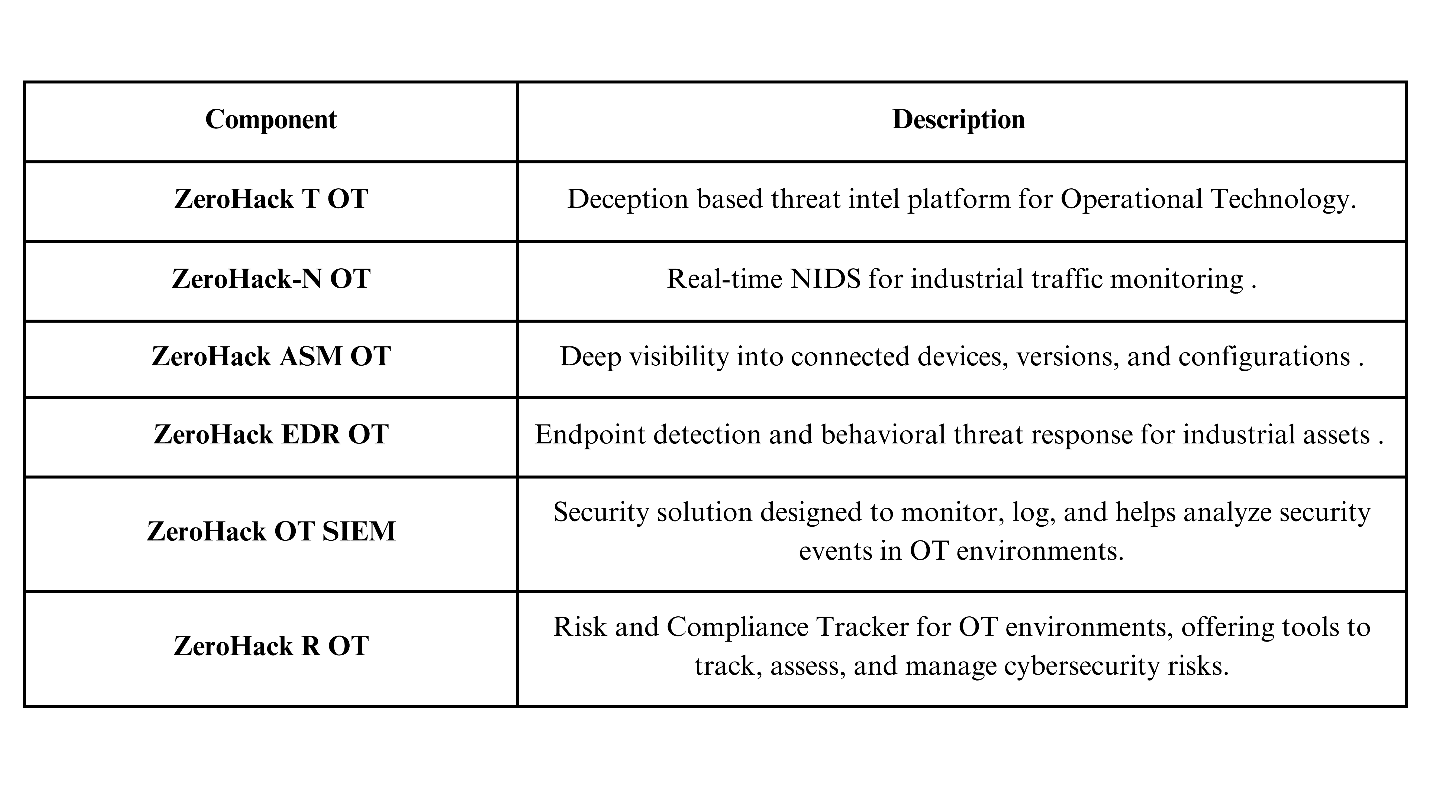
💬 Let’s Start the Conversation
- Are our OT and IT networks fully segmented with strict firewall policies?
- Are our legacy systems protected with compensating security controls
- How fast can we recover if ransomware hits our grid control systems?
- Are you compliant with NERC CIP, ISO 27019, or other standards?
Reach out to WhizHack Technologies today and schedule your OT Security Consultation. Together, let’s secure the future of critical infrastructure.




