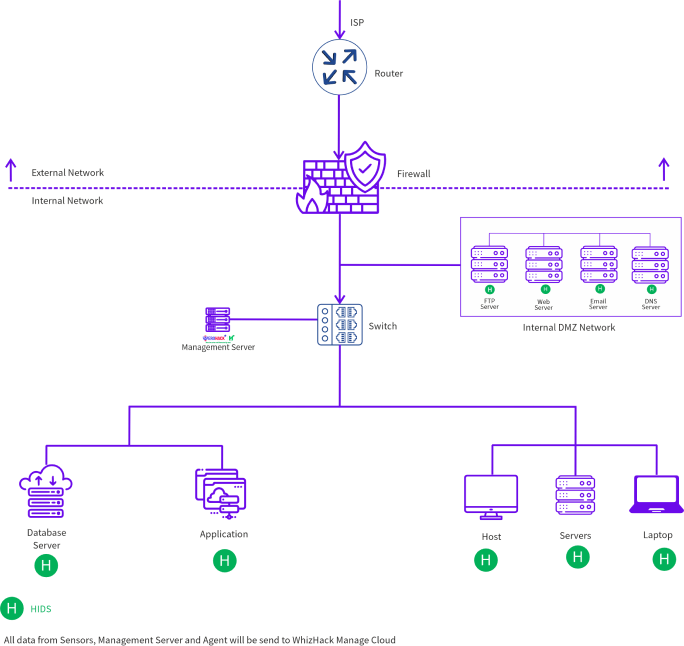
ZeroHack - H is crucial for cybersecurity, offering ransomware detection, vulnerability identification, log analysis, configuration assessment, and compliance support. With real-time alerts, customizable dashboards, and automated incident response, HIDS ensures quick threat mitigation and provides tailored reports for detailed security analysis.
Triple layer Engine
Probable Ransomware Detection
User Behavior Monitoring
Regulatory Compliance
Get Your Own Deployment Architecture