Network Intrusion and Detection System
Fastest network threat alerts with minimal false positives.

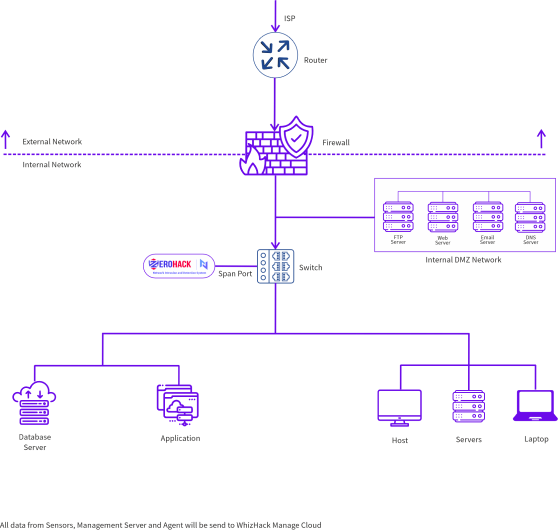
ZeroHack - N is a specialized Network Intrusion Detection System tailored for IT environments. It features a Triple Layer Engine for threat detection, which leverages models trained on extensive threat intelligence datasets. These datasets are generated through the deployment of the ZeroHack TRACE sensor across various platforms, including on-premises and cloud environments, in diverse geographical locations. This allows for effective analysis and monitoring of network traffic to identify potential threats.
Triple layer Engine
Behavioral Analysis
Real Time response
Integration with other Security Software
Security log analysis
Alerting and notification
Reporting insights Network Attack events

Get Your Own Deployment Architecture