Deception Technology based Threat Intelligence
Your Extra Layer of DPI - based Decoy on live traffic.

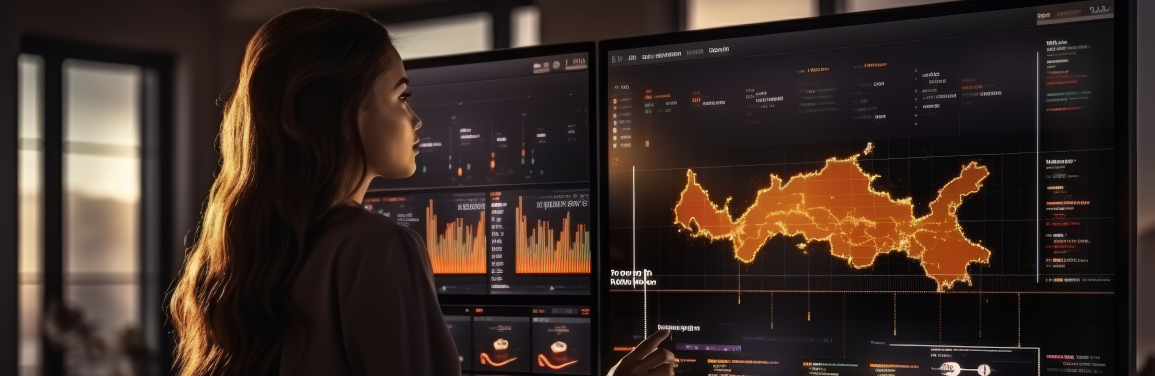
ZeroHack - T is a cyber threat intelligence framework using decoy technology and multiple sensors to generate and analyze threat data. It offers customizable, dynamic intelligent shifting sensors, easy reconfiguration, and self-healing. With a specialized DPI engine, ZeroHack - T captures real-time data for user analysis. Processed honeynet data enhances visualization and correlation, empowering analysts to secure networks comprehensively.
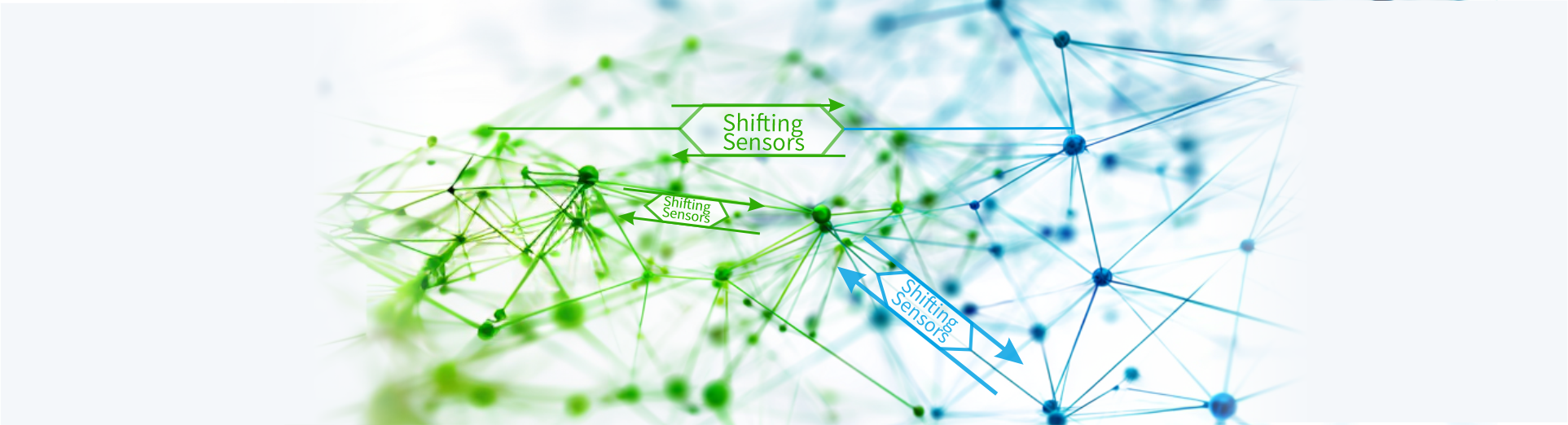
Proprietary Technology DISS® (Dynamic Intelligent Shifting Sensors)
Domain Specific Honeynets
Self-Healing and Auto Updating Sensors
Raw DPI Dataset for Attack Analysis
Re-configurable deception sensors

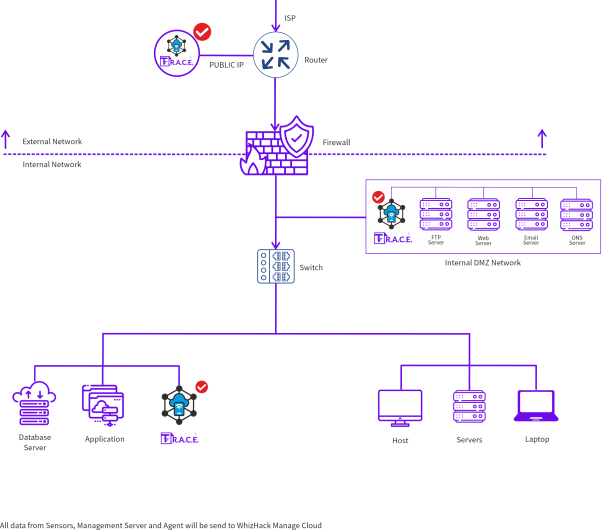
Get Your Own Deployment Architecture