
Vulnerability Assessment
Our cybersecurity service includes vital vulnerability assessments, crucial for pinpointing and prioritizing security weaknesses in network infrastructure, systems, and applications. Leveraging automated tools like network security scanners, we generate detailed vulnerability assessment reports. Regular assessments are imperative as cyber threats evolve, and new vulnerabilities emerge. Our ongoing vulnerability management program addresses technology and user-related issues, such as accidental data exposure, device loss, and malware installation, ensuring a proactive approach to prevent data breaches. Prioritizing and promptly addressing high-risk vulnerabilities is a key focus of our comprehensive service.

Penetration Testing
We specialize in providing penetration testing services, an authorized simulated attack on computer systems to assess security. Our testers employ attacker tools and techniques to identify weaknesses, simulate threats, evaluate system resilience, check controls, ensure regulatory compliance, and offer insights for management on security posture and budget priorities.

Vendor Risk Assessment
Ensuring cybersecurity in third-party collaborations is crucial to safeguard sensitive data. We offer comprehensive security audits tailored to your business compliance needs. Organizations often share confidential information with vendors, making vendor risk management a vital aspect of security initiatives. Assessing potential risks before entering contracts is essential in vulnerability risk management. Unauthorized access to customer PII through vendor networks poses legal, financial, and reputational threats. To mitigate risks, establish a strategy specifying data sharing, access, storage, destruction, and auditing frequency for each vendor.
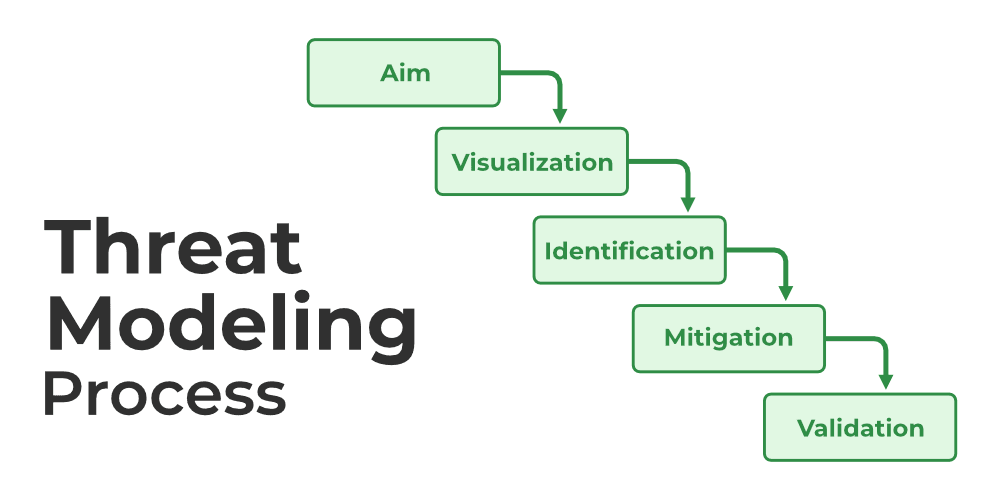
Threat Modelling
We offer cybersecurity services, including threat modeling—a structured process that aims to identify security requirements, pinpoint threats and vulnerabilities, quantify their criticality, and prioritize remediation. Our approach involves creating artifacts such as system abstractions, attacker profiles, and threat catalogs. By adopting the perspective of potential malicious hackers, we analyze software architecture and business context to gain a deeper understanding of system aspects. Typically performed during the design stage, our four-step process—Diagram, Identify threats, Mitigate, Validate—helps developers find vulnerabilities and make informed security decisions. Our goal is to assist you in building a sustainable security model for your services.
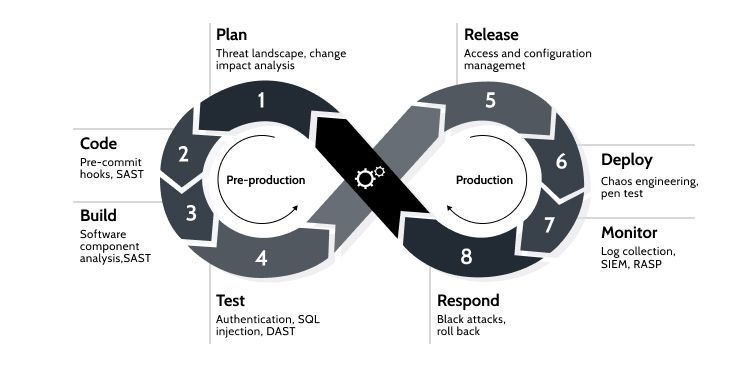
DevSecOps
DevSecOps, our cybersecurity service, integrates security into every stage of the software development lifecycle, addressing security challenges at DevOps speed. It's crucial in today's environment to mitigate cyber-attacks, offering specific benefits such as enhanced application security through automated tools, cross-team collaboration, streamlined application delivery, and the reduction of security vulnerabilities by leveraging automation. Emphasizing a security-first approach ensures a streamlined agile development process, minimizing unknown variables and positively impacting product release timelines.
Web Application Security
We offer web application security services to safeguard websites, applications, and APIs from a range of cyber threats. Our experts identify and address vulnerabilities that could compromise your product or service security. Common attack types include zero-day vulnerabilities, XSS, SQL injection, DoS/DDoS attacks, memory corruption, buffer overflow, CSRF, credential stuffing, page scraping, API abuse, shadow APIs, third-party code abuse, and attack surface misconfigurations. Our comprehensive approach aims to keep your web applications secure and functioning smoothly.

Mobile Application Security
We specialize in providing robust mobile application security solutions designed to protect enterprises from vulnerabilities and potential exploits. Our services encompass thorough scanning, utilizing the Mobile Application Reputation Service (MARS) to identify and remediate risks, enabling organizations to evaluate and mitigate potential threats. Additionally, we offer comprehensive hardening measures, including code obfuscation and anti-tampering features, to fortify mobile apps against both known and unknown vulnerabilities. Our active protection approach involves Mobile Runtime Application Self-Protection (RASP), which monitors app behavior, detects unusual actions, and safeguards against novel and zero-day attacks. In today's digital landscape, securing mobile applications is paramount for seamless business services. Leverage our experienced security experts to identify flaws and implement effective remediation plans, ensuring the utmost security for your mobile applications.

Infrastructure security
We offer cybersecurity services specializing in infrastructure security, safeguarding critical systems and assets from both physical and cyber threats. This includes protecting hardware and software assets such as end-user devices, data center resources, networking systems, and cloud resources. As enterprises increasingly rely on digital operations and data-driven decisions, securing technology infrastructure becomes crucial. Our experts conduct thorough security assessments and help establish the necessary security infrastructure, whether on-premises or in the cloud, to protect against a wide range of threats and ensure business continuity.
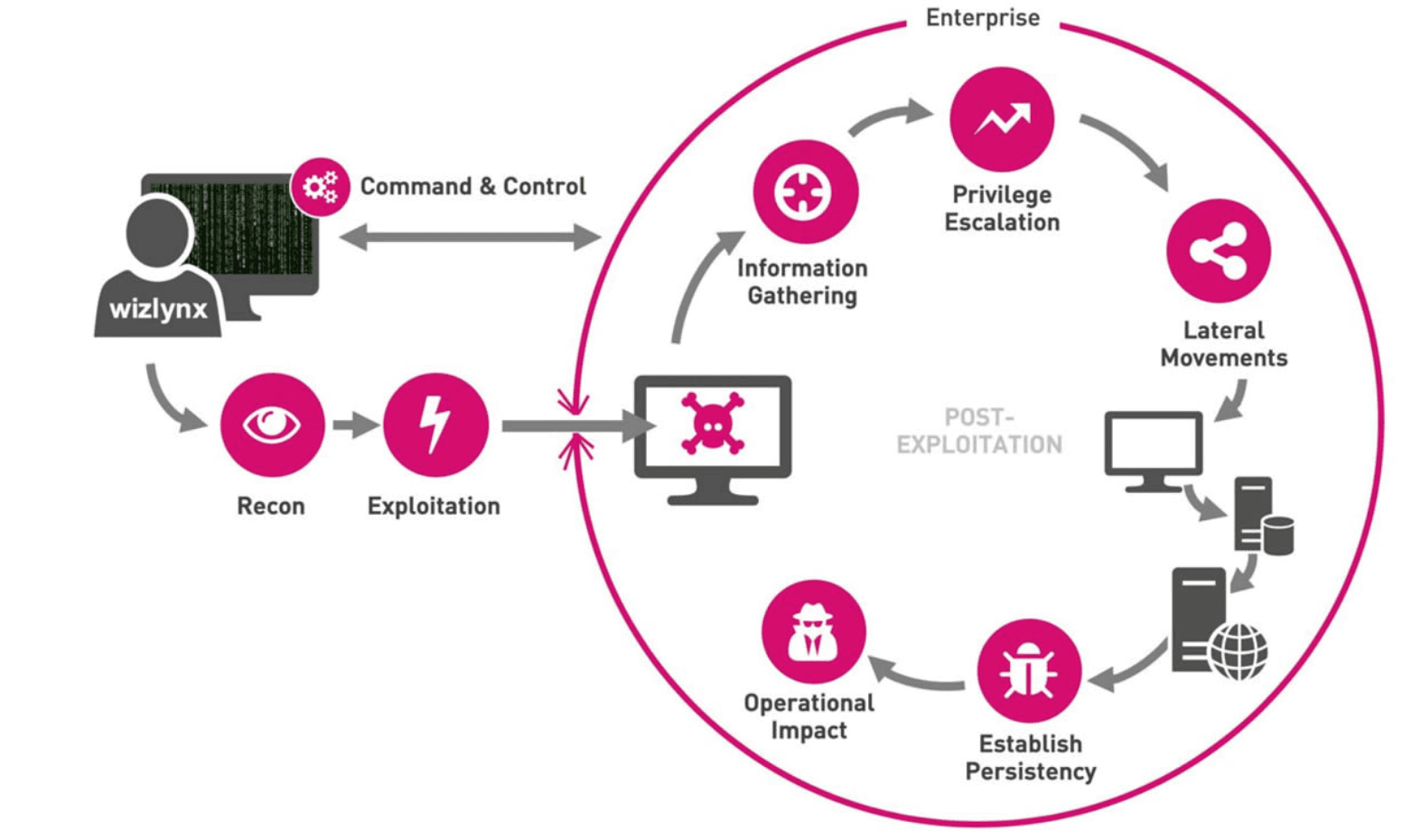
Red Team Exercise
We offer comprehensive cybersecurity services, including red team exercises—a simulated attack by skilled professionals to identify vulnerabilities. Our red team assesses physical security, network infrastructure, application resilience, social engineering awareness, and communication channels. This proactive approach helps organizations strengthen their defenses and reduce the risk of security breaches.

SOC
We offer cybersecurity services, including a Security Operations Center (SOC) with varying staff sizes based on organizational needs. The SOC employs people, processes, and technology to continuously monitor and enhance security, preventing, detecting, analyzing, and responding to cyber threats. Prevention is prioritized, with around-the-clock monitoring to detect and stop malicious activities. Suspicious incidents trigger thorough investigations, where SOC analysts analyze threats, leveraging global threat intelligence for effective triage. In the event of a confirmed incident, the SOC acts as the first responder, isolating endpoints, terminating harmful processes, and initiating recovery efforts such as system restoration and data recovery.